Cloud security is more than just an option today; it’s a foundational requirement for every successful company. Working with clients across every stage, I've seen how quickly an unprotected cloud environment can become a target. Azure Security Services delivers a well-thought-out, cohesive package of capabilities designed to shield your cloud resources, sensitive data, and critical applications from fast-moving cyber adversaries.
From my hands-on projects, I appreciate how Azure brings a depth of security tools that operate in concert to create a layered defense perimeter. These capabilities let companies meet compliance mandates, spot suspicious activity as it happens, and orchestrate rapid, well-coordinated incident responses. It doesn't matter if you're launching your first web app as a startup or juggling a hundred global subsidiaries in a multinational corporation, knowing how to harness Azure's security tooling has become a survival skill for cloud architects.
In this article, I’ll walk you through the most important Azure Security Services, highlight what each feature delivers, and show the tangible advantages for any company. We’ll move from core network protection right through to sophisticated attack analytics, giving you a clear roadmap for strengthening your cloud environment one informed decision at a time.
The Shared Responsibility Model in Azure
Understanding who is accountable for security in Azure starts with the shared responsibility model. This framework clearly delineates the duties assumed by Microsoft and the actions you, the customer, must be responsible for.
What Microsoft Manages
Microsoft secures the cloud by:
Managing the physical layer, including vast, secure data centers and the hardware inside them.
Protecting hypervisors, host operating systems, and the network infrastructure that connects them.
Ensuring that the Azure control plane itself, the platform services on which you depend, are reliable and secure.
What You Manage
You are responsible for security in the cloud, such as:
Encrypting and classifying your data to control who can read and write.
Controlling and managing user identities and their entitlements.
Configuring firewalls, private endpoints, and network security groups to filter traffic.
Applying secure coding, patching, and authentication to your applications.
Responsibilities Based on Service Types
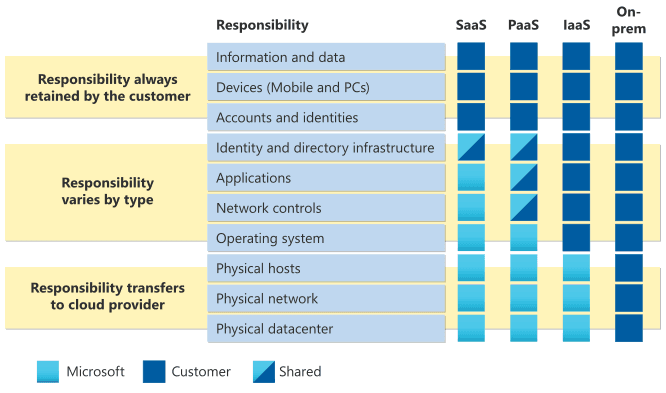
(Image source: Azure Security)
Your level of responsibility changes depending on the service type:
Infrastructure as a Service: You assume control of the operating systems, middleware, and network traffic filters.
Platform as a Service: Microsoft secures the operating system and middleware, offloading some workload but not all.
Software as a Service: Microsoft secures the application layer, while you still govern user access and data sensitivity.
Hybrid Cloud Considerations
In a hybrid deployment, the model broadens again. Ensure you:
Apply the same security constructs, identities, access controls, and network policies to on-premises and Azure environments.
Unified policies and monitoring systems must span both physical and virtual resources for effective and seamless threat detection.
How Azure Security Benefits Your Business
Azure Security Services protect your company while simultaneously improving your bottom line and your operational efficiency. This is more than defense; it’s a competitive advantage:
Scalability and Flexibility: Azure security capabilities expand automatically along with your company. Global scale and seasonal spikes impose no friction. The tools scale and reconfigure themselves in the background, allowing your team to focus on the expansion, not on security reconfigurations.
Advanced Threat Protection: Supported by AI and machine learning, Azure surfaces hard-to-spot adversarial campaigns. The algorithms ingest data from Microsoft’s worldwide security ecosystem, providing threat intelligence that is nearly impossible for an isolated team to replicate. They detect emerging attacks, even those never before recorded, before significant damage occurs.
Compliance Support: With in-built regulatory functionality and an extensive slate of cloud certifications, Azure makes compliance routines significant. Microsoft meets rigorous obligations such as SOC 2, ISO 27001, GDPR, and HIPAA, providing faster, more predictable paths through audits and easing the burden on your compliance team.
Saves Money: Consolidating security into a single Azure ecosystem and applying automation drives substantial operational savings. Rather than juggling and integrating point security systems from multiple vendors, you deploy coordinated, cohesive tools that require less overhead and simpler management. Customers commonly experience savings of 20-30% vs previous, disparate security architectures.
Azure Security Tools and Features
Azure's security framework is designed to offer modular services that protect distinct cloud assets. Understanding these offerings allows you to weave robust safeguards into your security architecture.
Azure Key Vault: Centralized Secrets Management
Azure Key Vault acts as the vault for sensitive payloads, housing items like passwords, connection strings, certificates, and encryption keys within one controlled boundary. Key features include:
A Hardware Security Module that guards cryptographic keys against unauthorized extraction.
Automated certificate renewal to keep services running smoothly with freshly minted, trusted certificates.
Granular access policies, enabling you to enforce the principle of least privilege with pinpoint precision.
Out-of-the-box integration with other Azure services streamlines the insertion of secrets into workloads.
Full-scale audit logging, ensuring that every access and modification is recorded to satisfy compliance regimes and forensics.
Centralizing secrets management through Azure Key Vault removes hardcoded secrets, mitigating one of the easiest attack vectors and reinforcing your security surface against leakage and misuse.
Azure Firewall: Advanced Network Protection
Azure Firewall delivers a cloud-native security perimeter fully aligned with Azure capabilities, ensuring scalable protection for your entire Azure environment. Key features include:
Stateful inspection across both network and application layers for comprehensive filtering
Threat intelligence integration that proactively drops traffic sourced from known malicious IPs and domains.
Granular FQDN filtering, allowing traffic control based on fully qualified domain names.
Deep packet inspection, extending into encrypted TLS (SSL) traffic without compromising the protection level.
Seamless support for hybrid environments, securing connections between cloud and on-premises resources.
Centralized logging with detailed records for compliance, audit trails, and investigative forensics.
Designed for enterprise demands, Azure Firewall provides built-in high availability, resilience, and capacity for multi-terabyte throughput across your entire Azure deployment.
Azure DDoS Protection: Defending Against Attacks
Azure’s DDoS Protection framework provides two tiers for safeguarding cloud applications from resource exhaustion:
Basic Tier: Automatically activated for every Azure service, offering core protection without extra setup or billing.
Standard Tier: Expanded safeguard that employs machine-learning-driven threat modeling, streaming attack telemetry, and 24/7 DDoS Rapid Response analyst support whenever an attack is in play.
Standard tier users receive enriched telemetry, comprehensive attack reports, and the ability to fine-tune resource defenses, enabling them to rehearse incidents and refine security playbooks without business interruption.
Azure Bastion: Secure Virtual Machine Access
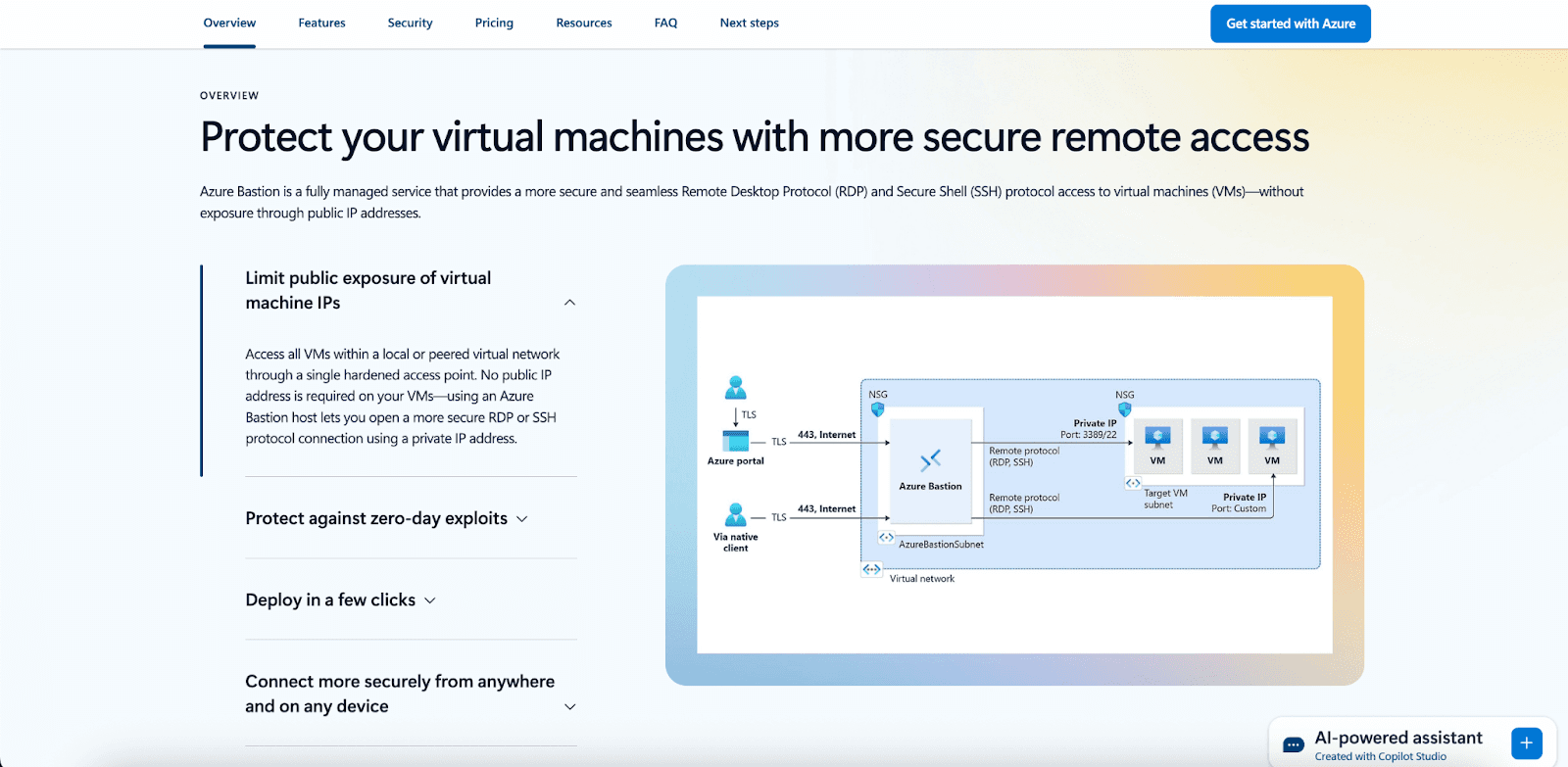
Azure Bastion secures browser-based, RDP, and SSH links to Azure VMs while keeping the instances free from public exposure:
Elimination of public IPs drastically cuts the accessible perimeter.
Unified connection oversight operated directly from the Azure portal.
Real-time session capture and cataloging to satisfy compliance.
Structured security protocols guided by VM access standards.
This capability ensures that IT personnel administer VM exposure with resilience, confidence, and full regulatory fidelity.
Microsoft Sentinel: Intelligent SIEM Solution
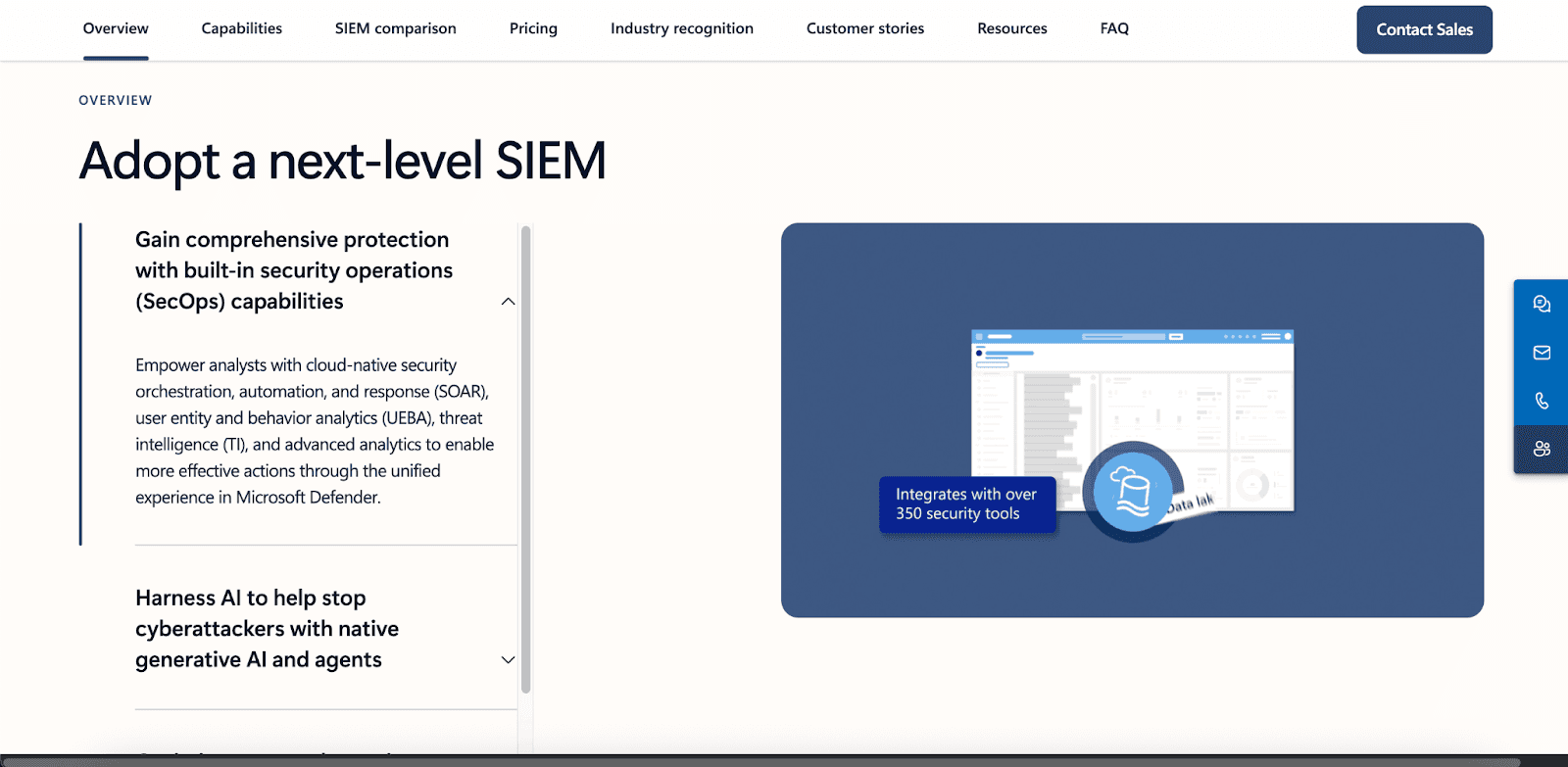
Microsoft Sentinel stands as a fully hosted SIEM and SOAR solution designed from the ground up for the cloud, delivering the following core capabilities:
Smart analytics driven by ML models that continually learn and minimize alert noise.
Response automation via tailored playbooks crafted in Azure Logic Apps.
A rich ecosystem of integrations that streamline workflows across the entire Security Operations Center.
Proactive, coverage-oriented threat detection spanning hybrid and multi-cloud environments to safeguard key enterprise resources
By unifying these capabilities in a single interface, Sentinel equips security operations teams to spot, investigate, and neutralize threats with exceptional speed and effectiveness.
Azure Monitor: Comprehensive Observability
Azure Monitor equips teams with comprehensive visibility into hybrid environments by aggregating and interpreting telemetry from both cloud and on-premises resources. Key features include:
Customizable dashboards and alerting rules can be tailored to address precise security and performance objectives.
Seamless integration with Azure Logic Apps triggers automated remediation whenever anomalies are detected.
Unified monitoring conjoins DevOps and SecOps functions, fortifying operational resilience across silos.
Compatibility with leading third-party monitoring platforms extends observability beyond Azure-native solutions.
Azure Monitor thus delivers the wide-angle view essential for effective security operations.
Azure Policy: Governance and Compliance
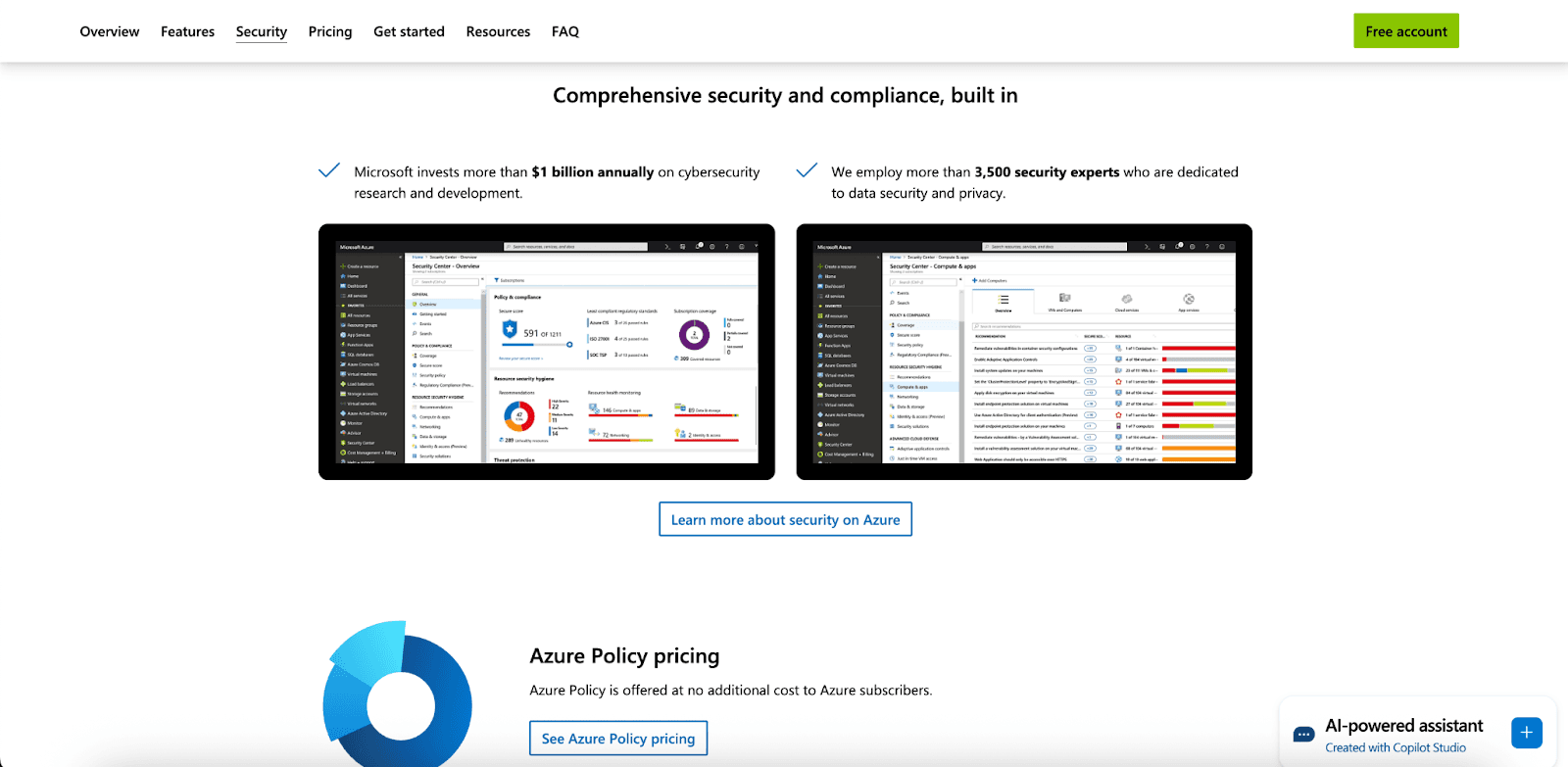
Azure Policy secures governance and compliance at scale by:
Regularly assessing Azure resources to verify alignment with formulated rules.
Silently blocking the creation of resources that deviate from set compliance specifications.
Mandating controls such as encryption, region restrictions, and the acquisition of mandatory tagging.
Providing out-of-the-box policy definitions targeting mainstream compliance mandates, including GDPR, PCI-DSS, and HIPAA.
By applying Azure Policy, companies preserve governance, diminish exposure, and simplify the audit lifecycle.
Choosing Your Azure Security Strategy
Choosing effective Azure security capabilities should reflect the company's scale, risk appetite, and compliance mandates. Use the following simplified guidance:
Business Size and Complexity: Smaller companies can secure core assets with Azure Security Center and Key Vault editions, while larger, more intricate environments often require the full spectrum of Sentinel and specialized threat protection solutions.
Industry Needs: Each company has its own must-address requirements. Healthcare must operate within the narrow lane of HIPAA, finance demands tighter data guardrails, and so on. Microsoft Azure has whipped up ready-to-launch blueprints that answer those varied call-outs straight off the bat.
Hybrid vs. Cloud-Only: If you’re running both on-prem and public-cloud shards of data, stick to protective layers that straddle both worlds. Seek features like hybrid threat detection and centralized policies that don’t require a repaint job every time you grow.
Risk and Budget: Tighten up the cost-security gear ratio. Go for the marquee-level safeguards only if that’s the price you’re prepped to pay, or pick the smarter, yet not second-best, guard that protects the same crown jewels for a smaller price.
Advanced Security with Pump's Secure
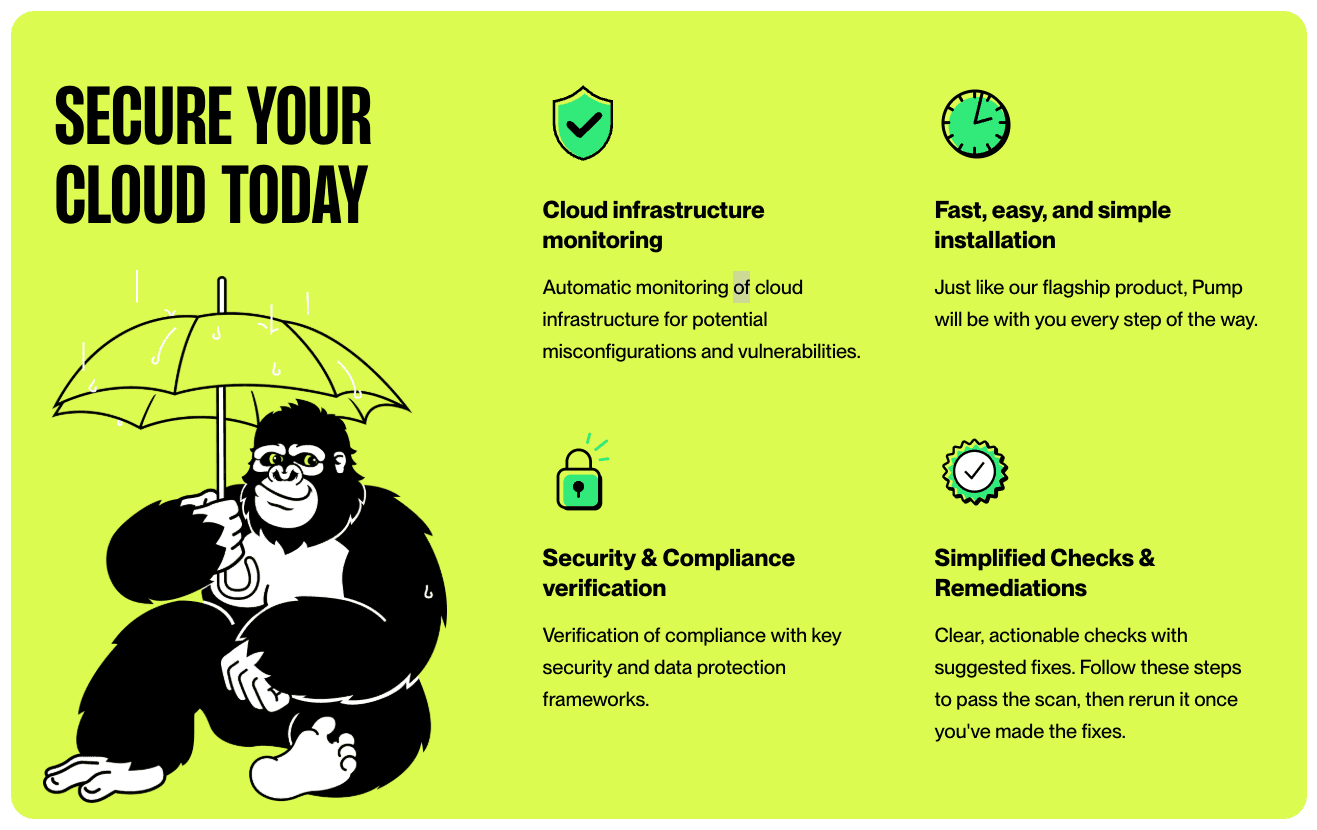
Pump Secure is a layer of advanced cloud security we’ve built on top of Azure’s existing protections, designed for companies that require far more than standard controls. You can activate it on top of your existing security stack with no complicated deployment.
Already available on AWS, we are rolling out an Azure version of Pump Secure that runs an automatic readiness audit against best-practice benchmarks. The audit executes 100+ security checks within five minutes, pinpointing critical vulnerabilities and misconfigurations that might undermine a hardworking system.
Here’s what Pump Secure delivers in a single, streamlined pipeline:
Complete Security Scans show every possible weak segment.
Detailed Compliance Reports document readiness against your sector’s standards.
Actionable Advice prescribes precise, fast corrective steps.
To keep operations smooth, we function in read-only mode, meaning it won’t interfere with your operations.
Cost Savings & Improved Security: Most security improvements immediately pay for themselves. Data shows simple configuration edits resolve about 45% of critical issues we discover, each adjustment that cuts cloud waste while lifting security and reducing cost.
Conclusion
Azure Security Services lay the groundwork for secure cloud operations, but effectiveness hinges on well-planned integration and continuous oversight. Start with foundational offerings like Azure Security Center and Key Vault, guardrails for critical resources. Layer on Azure Firewall and DDoS Protection to harden the network, and, for teams with mature security programs, import Microsoft Sentinel to elevate threat visibility and streamline incident response.
Security isn’t a destination; it’s a perpetual cycle. Conduct routine risk evaluations, refresh governance policies, and keep your teams educated to keep pace with shifting threat landscapes.
Looking to strengthen your cloud security posture? Request an Azure security compliance report, book an Azure SOC demo, or activate a trial of Azure security services to put the platform to the test.




